False-positive ASR Alerts: Block execution of potentially obfuscated scripts
Quick one, because I know this happens, but can't see any blog posts about it.
Because many Microsoft Office (Word, Excel, and PowerPoint) components and add-ons now use the web and the JavaScript APIs, it is expected that they will sometimes download and use JavaScript files. This is mostly unnoticed, but in some corner-cases, I've seen cases where Office products have created false-positive Attack Surface Reduction (ASR) alerts.
In the Defender for Endpoint portal, you may see alerts/events with "WINWORD.EXE was blocked by the attack surface reduction (ASR) rule "Block execution of potentially obfuscated scripts", and a process tree showing Office writing a file like C:\Users\*\AppData\Local\Microsoft\Windows\INetCache\IE\*\odsp.react.lib-ad0d5d04[2].js
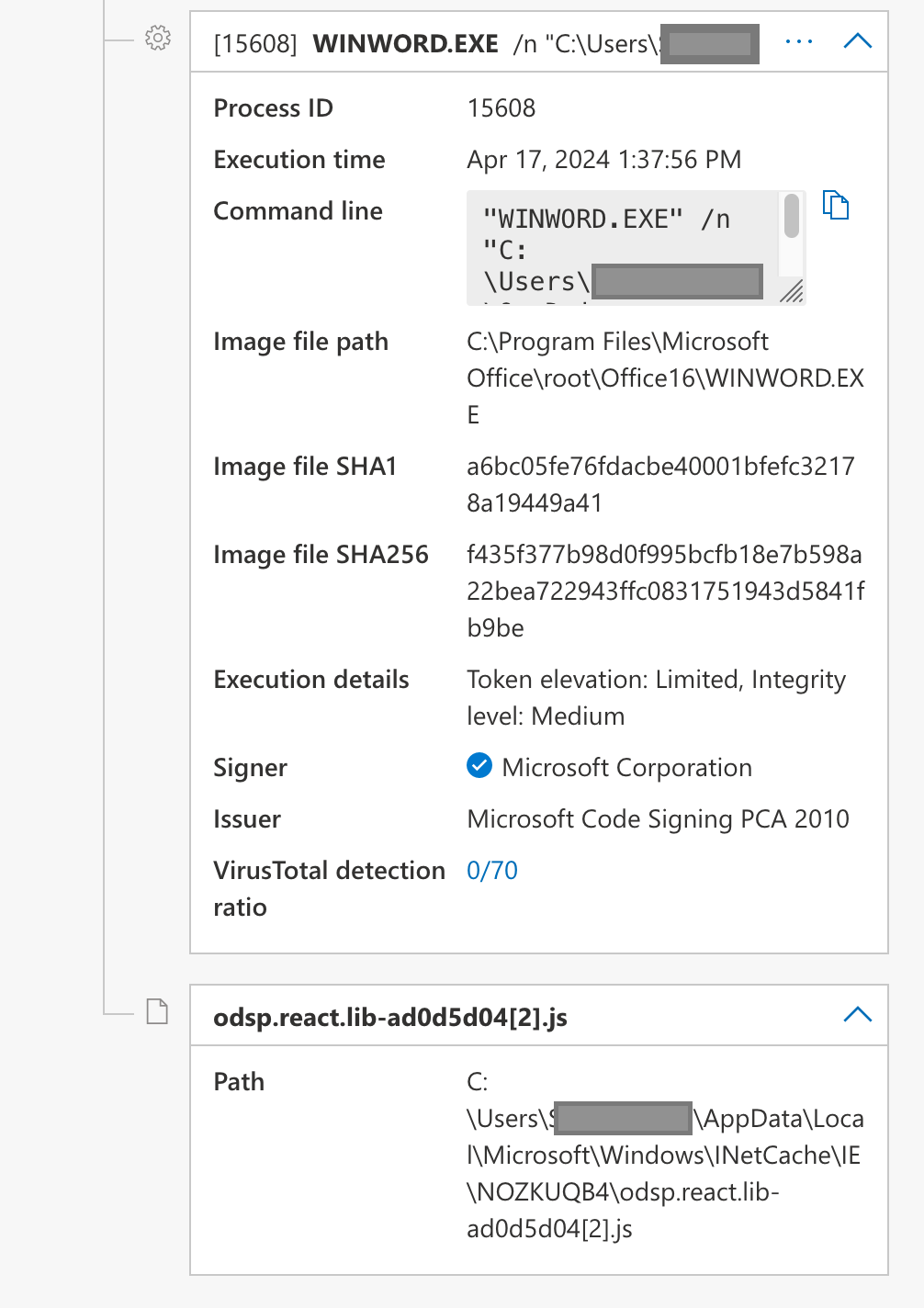
To verify if this is a false-positive, look around the Timeline for the file creation event (usually within the same second, but can be after the ASR block event... because concurrency is hard.)

Grab the filename, and try to download a copy from the Microsoft source. In this case, the ODSP library is hosted from https://res-1.cdn.office.net/files/sp-client/odsp.react/odsp.react.lib-ad0d5d04.js - here's a CyberChef recipe for the lazy.